Every year in the summer, thousands of hackers, nerds and journalists descend on Las Vegas for the annual “Hacker Summer Camp” or the back to back conferences of Black Hat and DefCon (along with others).
And every year, the same discussions, tips, and tricks are doled out regarding operational security—or OPSEC for short—while travelling to the conferences. To take the technical definition from NIST:
OPSEC is a systematic process by which potential adversaries can be denied information about the capabilities and intentions of organizations by identifying, controlling, and protecting generally unclassified information that specifically relates to the planning and execution of sensitive organizational activities.
Fancy definition aside, think of OPSEC as “covering your digital ass.”
As our friends Runa Sandvik, The Grugq , and others have preached time and time again, OPSEC looks different for everyone and every circumstance. It requires thought, planning, testing, and risk assessments throughout to ensure that you are applying the appropriate level of paranoia while not overspending or creating opportunity costs.
It’s a process, not a checklist.
We all know "that guy" who runs some esoteric Linux laptop that takes him 15 minutes to boot up. It's complete with a USB-key, isolated applications, and a Chrome browser so neutered it couldn't squirt an extra thread if its life depended on it—just to show you a picture of their cat (cute, by the way).
And they'll tell you that you are the crazy one for running a MacBook Pro.
At Permanent Record, we do not consider ourselves experts in OPSEC; we are only students, thankfully, so we avoid most of those conversations.
There is also a certain level of what is called "user awareness" training that takes place. This training—either literally a course or via the hard-knocks method—is designed to teach the average user about cybersecurity risks, how to avoid phishing scams, and how to best protect themselves.
So, we often think about the "big" things as journalists or technicians. The VPN turned on when you travel, two-factor authentication on your social media, don't click on weird looking links. You know, the usual shit.
But a big part of what Runa and The Grugq have been preaching is risk assessment as a central component of this process. You can't read a how-to article from some CISO magazine and apply it to yourself as a journalist or student. You have first to understand what your risks are before you design defences.
Let's use a relatively humorous example that doesn't involve nefarious hackers or a nation state. It involves yours truly and the OPSEC risks of news clippings to podcasters.
Newspaper OPSEC
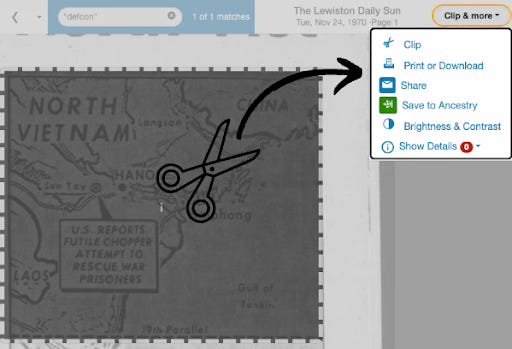
We have ranted and raved about how much we love newspapers.com and its incredible utility in online investigations. If you haven't used it for research, I highly recommend you do so, not only for its depth of archival materials but also for some of its simple clipping and snipping tools.
By snipping and clipping, you can either download them to your hard drive (what we do at Permanent Record) or save them to your Newspapers.com account so that you can refer back to them later, create collections, or collaborate with others.
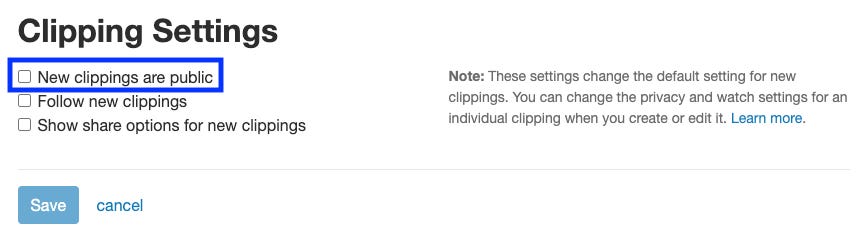
Much like social media, these clippings have privacy settings, which allow you to allow others to see them or not.
I always like to pay attention to this because it may tell me that someone else is looking at a case and may have located other news articles. So, I will click on their profile and scroll through any other clippings they have.
Other times, you may see a username that trips your memory, say something like “PopularPodcast” (not a real name), and your poorly trimmed eyebrows may shoot up like mine did.
PopularPodcast is very popular. It had been in the true crime top 10 for years. It was a staple in many playlists and universally loved by its fans. Tens of millions of listens or more, we'd have to guess.
When I saw clippings for a PopularPodcast username, I thought it was perhaps a fan, like me, who was an avid listener and subscriber. However, after one click on their profile, I realized that it seemed a little too well organized.
The clippings were in chronological order of PopularPodcasts episodes.
I could also see what they were working on for current and future episodes.
At this point? There are two wolves inside of me, as you can imagine. To be able to shoulder surf—entirely legally—over some of the best storytellers in the world would be incredibly fun.
But it was non-consensual. It's not like they had a page on their website saying, "Hey, come watch us work!" I knew they would not have done this on purpose. So, alas, the right wolf won.
I quickly emailed the show's producers and told them I had spotted it and to quickly fix their privacy settings.
They responded!
And fixed it, and were incredibly grateful that I didn't just start scooping stories or leave them vulnerable to a significant business and OPSEC risk.
That's right, along with the usual risks that a journalist will face, podcasters have a separate OPSEC risk that they must manage.
Podcaster Risk Assessment
At Permanent Record Research, we are a bit of an anomaly in that we share our work and post documents, are not interested in 'scoops,' and are far happier to collaborate with others rather than protect or sit on a story.
However, we benefit from not being driven by advertising dollars or competing solely in an increasingly diluted content market.
This is one of the risks to the average podcaster, particularly if you are a Top 10 True Crime show. A big part of your draw is being able to tease out and find stories using your unique research methods, coupled with unique storytelling.
Applying this lens, we can see that a significant risk to your business would be someone observing what stories you are working on before you publish them, ascertaining the timing of your releases, and front-running you with the content just before your scheduled release.
With little effort, a 2 to 5-minute YouTuber can make it look like they are both better than your podcast, can hitch their wagon to your larger brand identity, and potentially—eventually—start to convince advertisers and others that they have the best and most topical content.
This isn't journalistic paranoia. This is exactly how digital theft and corporate espionage work. Information is valuable, even the stories and timing of what the biggest journalists and podcasters in the world are working on.
So before you head to Las Vegas, Newspapers.com or Facebook, think about yourself and your risks. Jot them down.
Then think about each service or thing that touches those risks, whether it is social media, a research subscription or even a passive watcher of YouTube.
Now, turn off every privacy setting you can without impacting your bottom line.
Monitor.
Rinse.
Wash.
Moisturize.
Repeat.
Now go have fun in Vegas, folks, and be safe!