Hunting Alexa: The Subtle Art of Deanonymizing a Child Predator
Part One. Catch Part Two on October 23rd.
I was reading through old Yahoo instant message logs from 2006. These chat logs were between two individuals discussing their mutual interest in the sexual abuse of children, a sort of brainstorming session on how to create the content, how to find young girls, develop opportunities to groom them, and worse, how to drug them if needed.
This was dark shit.
As I was reading, I was surprised by the relaxed nature of the conversation. It was casual, as if this was a challenging work project that needed discussion, but no inkling of moral or ethical sober second thoughts.
Reading this decades-old chat, I wondered how they could converse with such normalcy and a casual disregard for what they proposed needed to be done to children.
I needed a break.
I rolled my chair back and bumped into my son's Hot Wheels track. It toppled over.
"Ah, shit," I muttered, annoyed.
As my youngest was getting older, his race tracks were becoming more complex. They coiled around the basement in various directions.
I slid the length of track away from my desk and chair. I fixed the precariously balanced track I knocked over—on a box (to make a ramp, obviously)—and looked around the basement. Toys. A small table covered in construction paper usedfor art. A giant Rubbermaid container of superhero costumes. A Fisher-Price Basketball hoop.
I don't actually have an office in my home. I share the space where my kids play—my giant monitor, whiteboard, and chair existing as this professional alien creature dwelling in a space filled with toy cars, Little People, and Paw Patrol action figures.
This was my chaotic work-from-home situation, but it worked. On days he was home with me, my youngest would play while I typed away on my keyboard. I could hear him happily imagining a complex race between competitors, his little voice and brain engaged in self-talk.
I looked down and used my foot to roll a small green car away from my work area. He wasn't home today. The house was empty.
I looked back at my computer screen. The PDF was still open with dozens and dozens of chat logs, all related to child sexual abuse material, and then I looked back at the kid's toys.
The juxtaposition of these two situations, one filled with kids playing and drawing and dressing up as Jedi from Star Wars and a conversation between two adults working out plans on the best strategy to sexually abuse a little girl, slapped me so hard, I could taste metal.
“you owe me. check your email.”
The message from Alexa came at about 1:45 AM on a random Tuesday in October 2006. The receiver of this message and the email responded a minute or so later.
”wow, these are nice…that last one is awesome”
Those images and these messages helped put a man in prison over a decade ago. But Alexa was still out there. The police didn't or couldn't track her down. According to trial testimony of the state's computer forensic analyst, when asked about Alexa's identity, "I didn't even try. It wasn't a priority."
Reading through Alexa's chat logs, she was clearly the expert in the chat room, and clearly older; with access to a large repository of CSAM (child sexual abuse material), she knew a lot about the subject.
With all these logs, the only clue I had was an email address she used back in 2006.
The hunt was on.
The older an email address gets, especially with nearly two decades gone by, the trail can grow cold. It is doubtful this email address is even used anymore, so records may be scarce. Google provided nothing of value, at least at first.
I decided to turn to the Darkside—breach data.
It made sense to start here. Older data leaks will contain older data. I was looking for old.
Now, I've used a lot of breach data tools. From fancy pricy ones to free ones (RIP 0t.rocks), but I have to be honest, the best one I've ever used is Darkside by District4 Labs. No, I'm not being paid to say this. I rep what I love (looking at you Coke Zero).
They have an API, and they integrate into all the things, like Maltego. I use Darkside’s in-house UI web version, because I like to kick it old school (and I can’t afford Maltego, hah).
Start at square one. An email address.
alexa***@yahoo.com.
Bam! 23! Holy shit.
Ok. First, I was able to see the various passwords Alexa used. This could be useful. Not because I would access accounts (that’s illegal), but because with the more unique ones, I could run searches on those passwords to see if they link to any other possible users.
This is why I love Darkside.
You can search a lot of different selector types. So, a unique password can be run against their database, and if you find other hits with that same password, it could be the same person.
Now, what’s even better is that you can “Search within results.” So, if you get hundreds of hits back, you can narrow that down by searching for keywords that could appear in the breach logs. It’s saved me a lot of time in the past.
Alexa was a busy bee, but many of these breaches contained little more than user IDs (which would be useful if I were law enforcement and could file a warrant, but I ain’t) and passwords like “69fun” and “xxxxxx” which seem like pretty common ones. I wrote them down in my notes, and decided to keep moving down the list.
Hit #16 was interesting. It noted a name, “Lex T,” and a username, “sexylexiT.”
Useful, but it wasn’t a home run.
And then…#22 of 23.
A gambling website breach.
I remember smirking. Cautious optimism. An apartment address in Los Angeles and an IP address.
I added this to my notes and performed side searches on Alexa*** as a username or alias without yahoo.com. No new hits, unfortunately. I also ran the email address again and turned off the “Strict” setting, which will run various similar iterations of the Alexa*** email. It found a handful, but they contained no new information.
I ran the apartment address in LA and came up with several hits. My assumption was that Alexa wasn’t a real name, so I noted all the selectors of the various names who had breach data linked to that address. There were four other names that were connected to that address, but there was no direct link between them and Alexa I could see.
It was time to investigate what existed outside the dark, murky world of breach data. What could I find out about Alexa on the surface web?
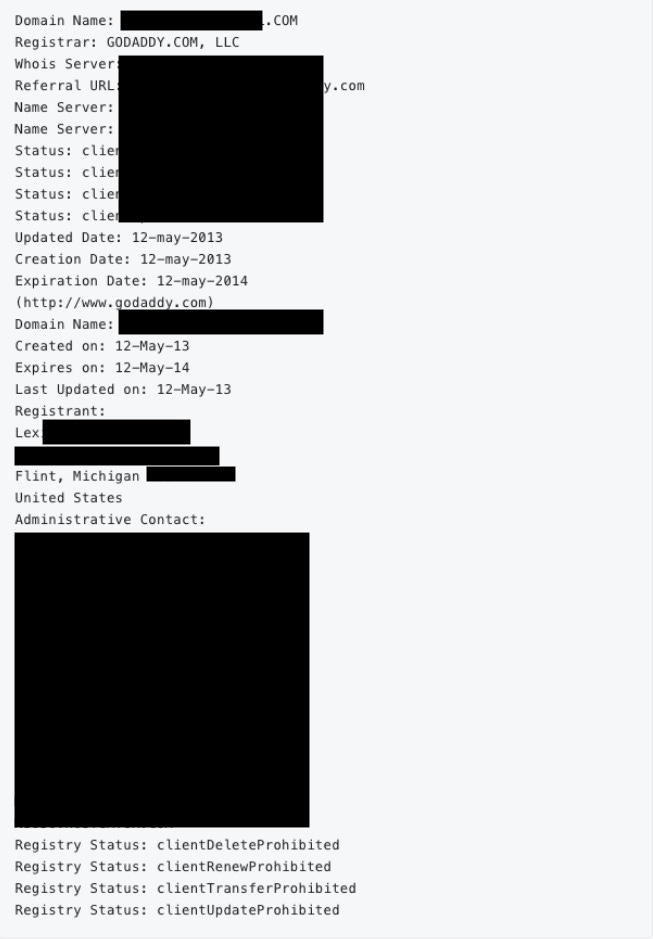
I then turned my attention to searching for domains. I don’t usually do this so early in my investigation, but I knew I was dealing with a very old email, and I knew doing one quick search would just let me cross it off my list of attack vectors.
I assumed there would be nothing here, but when I punched in Alexa’s email into DomainIQ…
Holy shit!
A name!
Lexa Trenton (not the real name, as aspects of this case are still open).
A domain!
www.***productions.com (Sorry.)
A phone number!
619-9**-***5 (Wish I could tell you, but I can’t).
And an address!
742 Evergreen Terrace in Flint, Michigan (not real).
I assumed that Lexa Trenton was as good as caught. I assumed that this Hot Wheels track was simple, but much like the one that occupied my basement, the forks and twists and turns were still coming. I assumed I had her. I assumed this investigation was over.
I was wrong.
Part 2 of “Hunting Alexa” will be out on October 23rd.