A Free OSINT Lesson: How Many Shell Companies Does This Guy Have?
Essentially, how OSINT Industries saved our asses
We have this ongoing case at Permanent Record Research. We humorously, and fittingly, refer to it as our “Whale.” I can’t say much beyond the fact that it’s big and complicated and has a lot of weird moving parts.
One of those moving parts was a young man running a series of shell companies that engage in various, albeit curious, money-making ventures. The legality here is grey because those companies exist in places like the British Virgin Islands, Cyprus, and the Caymans.
You know how it is.
You need to hide money from your government. You need to avoid certain laws requiring very specific licenses to operate. You need to move money around quickly and easily via cryptocurrency. You want to avoid a lawsuit filed against one of your companies in the United States.
It’s grey as fuck.
Before we get into it, we at Permanent Record do a lot of work like this. If you are interested in knowing more, or curious if we can help, feel free to shoot us a message here or an e-mail here.
Wading into this, I have a decent amount of selectors on this guy. There is a website domain (operational and earning money), a company name (based in Cyprus), and a lead on a Discord username.
Finding the Discord username and the user himself was fairly easy. He was pretty active. Using a burner Discord account, I started hanging out in the channels he was in. I started reading his various posts. I found some photos he posted of some meals and places he was visiting. Essentially, I got a pretty good idea of the man himself. I knew he was an Italian national who spoke very good English. He talked about some of his business dealings on various servers but never gave away a name or anything specific like other websites he may have owned. But based on the messages, this was clearly my guy.
Now, I just needed to deanonymize and find him…
Domain searches were useless here. Cloudflare has been hosting the site since its inception. I try to get around the "bulletproof" hosting via some Linux tools that can sometimes show you a true IP address, and I ran some pentest tools to see what I could gather about the site, such as other domains or email addresses (we won't share them here, so do some research I guess, or shoot me a message). No luck. The shit is locked down.
Open Corporates gave me next to nothing about the shell company. There were some interesting details about the lawyer who set up the company in Cyprus, and that led me down an interesting rabbit hole, but since it was no longer connected to the "whale hunt," I decided to double back. Let's just say that Cyprus is a great place to hide company ownership and your paper trail.
So, I turned to the website itself..
Now, for all you new and budding OSINTers, the first stop on any website you are investigating is the Privacy Policy and Terms of Service. Sometimes, it'll say a company name, and often, it will have an email address. My advice is to just "CTRL-F" and type in "@." If nothing pops up, try typing in "at."
In this particular case, it was "admin@***MJishuntingyourass***.com."
Now, I've said it before, and I'll say it again—OSINT Industries is a really great tool here. Yes, this is a plug. And yes, I'll include a link for you below.
Simply put, it's easy, it's fast, and it works damn well. Oh, and I don't need to boot up my Linux VM, open a Docker, or run a command line.
Listen, I'm a busy person.
I'm a father of three small kids. I have an old giant cat who throws up during work calls. So between cooking meals for my family, grocery shopping, soccer and swimming lessons, cleaning up cat vomit, and occasionally human vomit because my six-year-old got the flu, again, from snot-nosed Parker at school… because Parker's parents just send him in regardless… taking 5 seconds to run an email address is way better than taking 10 minutes to boot up all that virtual machine shit.
So I pop that "Admin" email into the OSINT Industries search bar, and it runs through all these modules to find where it's being used. It runs hundreds of searches for you. Again, it's just... nice. Smooth. Effortless.
Anyway, I got one hit. A Google account. However, no useful information. All anonymous. Shit.
At this point, I realize I need a Coke Zero. I dodge the cat vomit on the carpet on my way to the kitchen, check on that homemade ragu I've been cooking for the family, and reach into the refrigerator, silently cursing Parker's parents for sending him to school with a fever and a violent cough, and retrieve my favourite elixir. As I crack that Coke Zero, I realize that I have been a fool.
Sitting back down, I open a new search on OSINT Industries. I have my target's Discord username. How likely is it that he uses that username for his company email? He does want to remain anonymous, after all. So, I type it in.
“target’susername@***MJishuntingyourass***.com”
OSINT Industries finds three items. A Google account, a Microsoft account with no personal details, and a Trello account…with a personal name… an honest to goodness Italian first and last name.
Holy shit.
Now, this guy has scrubbed himself off social media. Sure, he has accounts, but they've been wiped and locked up, and all the privacy settings are set to the maximum. I found various social media accounts, but they were wiped clean. I did some internet archive digging, but nothing. There are no photos of this guy. Anywhere.
I take another sip of Coke. My cat throws up again. Parker's contagion infects my son at lunch when he sneezes on my boy's sandwich. The ragu smells great.
I turn to breach data. I punch in the Italian name and run a search. I get two different email addresses connected to the name. One is Gmail and one is Yahoo.
Dope.
Back to OSINT Industries.
The Gmail email address turns up a lot, but it's not my guy. Same name but the details don't match. My target is maybe 23 or 24. This dude, clearly in his 40s.
I punch in the Yahoo email.
“Italian_Name@yahoo.com”
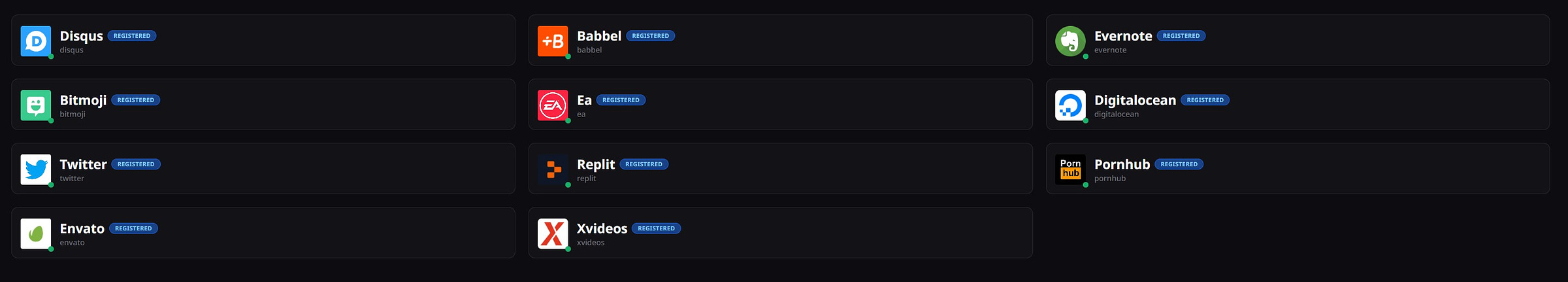
I get peppered with hits. Pop Pop Pop. This guy has accounts under this email everywhere. There must have been 20 or 30. As I mentioned, most were scrubbed, so no photos anywhere… but there were two hits which unlocked a whole world.
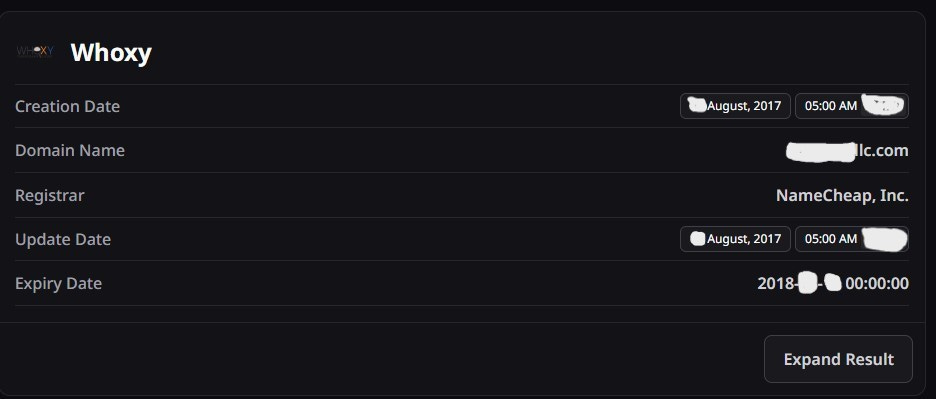
The first was a Whoxy hit for an old domain registered to the personal email address.
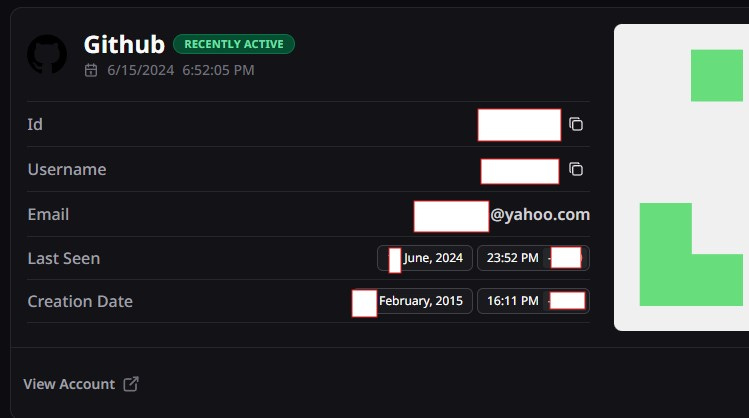
The second was a Github hit.
Suffice it to say that the Whoxy hit opened up a search to an entirely new series of shell companies owned by the target, all related to a similar industry. With this, I found other email addresses for the same individual, both personal and work-related. This led to more usernames and more accounts. This guy owns a lot of shell companies.
I found companies in Italy, the Cayman Islands, the British Virgin Islands, and England. I even found one in the United States, where, to paraphrase Shakespeare’s comedy A Midsummer Night’s Dream, “The sharp American law can pursue…”
The Github was the icing on the cake. While some of it was set to private, his repository was public and quite literally contained the code he uses for some of his “grey” online activities. Moreover, he had a defunct personal website URL, again, with another email address.
I ran nearly two dozen searches in OSINT Industries for all this, and each run revealed more information about this guy. I found his address in Italy, two phone numbers (which I also ran through OSINT Industries), a European business license, a VAT tax ID number, and even the names of people who started businesses with him in the past.
Oh, and just for fun, he also has a Pornhub and XVideos account (for my long-time readers, you know my penchant for finding targets via their sexual proclivities).
At the end of it all, an investigation that would have taken weeks took just days. While there was some investigatory gumshoeing here, the ability to quickly pivot to this search tool and make CSV or PDF copies of the reports with a single click makes life much easier.
Now, when I explained all this to our friend Nathan at OSINT Industries and told him I was going to write about it, he said he’d give us an affiliate link to provide for our fine readers. There is a discount on the service and everything!
He even offered to pay us for the post, but we told him to “fuck off.” It was all very polite. We laughed.
Visit OSINT Industries and use the code BS25 at checkout. It’s worth it.
With all the data we’ve exported on this Italian guy, we’ve discovered at least a dozen companies. Perhaps someday, you’ll see.